
10 CVE Scanner Must-Haves for Security Success
Thanks to a thriving open-source community, more projects, solutions, and open-source code are being produced than ever before. And while development organizations can find open-source solutions to be greatly helpful, the quality of code varies widely. The same can be said for commercial software.
Thanks to the Common Vulnerabilities and Exposures (CVE) database, thousands of software vulnerabilities are reported and tracked. As the proliferation of software continues to increase, so do the number of vulnerabilities in the CVE database. In fact, 2021 reported the highest number of submitted vulnerabilities in history with over 20,000 CVEs. Left unchecked, embedded developers may be leveraging software in their code base that contains critical security vulnerabilities and be completely unaware of it. The security risks this leads to are significant, with Forrester reporting that nearly a third of all external security breaches are caused by software vulnerabilities (Forrester – The State of Application Security, 2021)
Embedded software development teams need strategies and tactics to address the growing risk of security vulnerabilities in their solutions. Wind River has been supporting embedded developers for decades through software solutions and expert professional services and has strong expertise in security engineering required to address the impact security vulnerabilities can have on embedded systems.
It is through this experience that we offer 10 must-haves for CVE scanning and addressing security vulnerabilities.
1. Develop a Vulnerability Management Lifecycle
As development teams continuously update their products, code changes constantly. New additions, refactors, imported packages, third-party code, and countless other alterations affect the state of a code base at any given time. Given this reality, vulnerability scanning can never be a “one and done” activity.
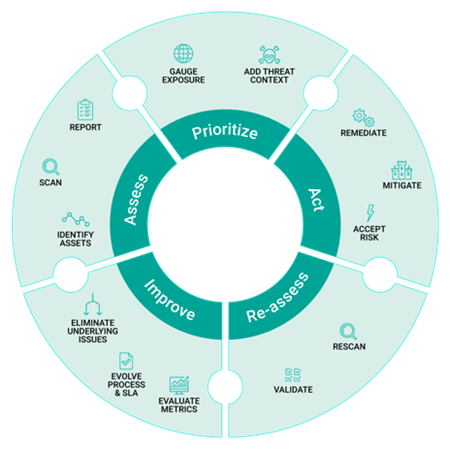
Development teams need to manage vulnerability detection as a lifecycle that includes constant assessment, effective prioritization, scanning and detection, and finally a method for growing the library of known vulnerabilities so detection can improve over time. Ultimately, applying a vulnerability management lifecycle will dramatically lower the risk of platform and application code and the exposure to a potential security breach.
2. Accuracy
The CVE database is growing faster than ever, and the number of known vulnerabilities is at an all-time high. Unfortunately, there is no sign this trend is slowing. The threat landscape is increasing, the number of threat actors is high, and the sophistication of security attacks is troublesome.
A good number of these known CVE’s, however, are irrelevant for embedded developers. A key success factor to effective vulnerability management is parring down the world of CVE’s to a curated database of those vulnerabilities that have the most impact on embedded development teams.
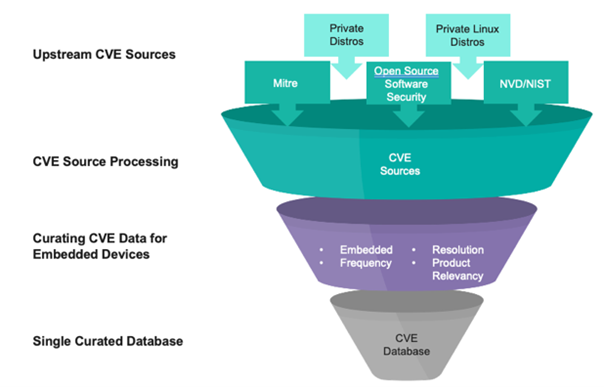
Through CVE triage from multiple sources, Wind River has built a vulnerability database that is tuned for embedded development. Software development teams can then use this CVE database within the vulnerability management lifecycle to keep scans targeted and relevant. Not only does this reduce the amount of time and resources required for vulnerability analysis, but developers can leverage the experience Wind River has developed for addressing security vulnerabilities.
3. Stay Current
Vulnerability scanning is only as good as the source, however, which means that maintaining a current vulnerability database is crucial to successfully address security risk. New vulnerabilities are submitted to a variety of sources on a daily basis, including the National Vulnerability Database, Mitre, and other repositories. Staying up to date on relevant CVE’s across these numerous sources is arduous to say the least.
Using curated sources designed specifically for embedded development teams like the Wind River CVE database is a key success factor to staying up-to-date with the most relevant CVE’s. Using sources like this, teams know they are always scanning for the latest known vulnerabilities.
4. Automated Vulnerability Identification
A structured approach that Wind River recommends is to take advantage of automation to help with vulnerability detection. This starts with creating a software bill-of-materials (SBOM) – a precise list of every software package being used in the Linux OS platform or application. Wind River solutions can help create this enumeration of components so you always have an inventory of packages in use.
SBOMs, which use the software package data exchange (SPDX) fomat, includes not only descriptor information, but version, name, license, manufacturer, and other metadata associated with the software package. By using this information, developers can create a powerful inventory of software that comprises their Linux OS and/or application.
This then becomes the foundation for intelligent vulnerability scanning that is tailored to the software in use.
5. Triage Efficiency
Like many organizations just starting a vulnerability assessment process, there’s a good chance that initial scans will prove to be overwhelming, sometimes finding hundreds if not thousands of vulnerabilities in large code bases.
A challenge, however, can be knowing where to start. The Common Vulnerabilities Scoring System provides a severity score for every CVE tracked. The Wind River vulnerability scanner can uses this score to deliver a prioritized list of CVE’s that have the highest impact on the code. Using the CVSS score, developers can zero in on the vulnerabilities that have the greatest risk to their solutions.
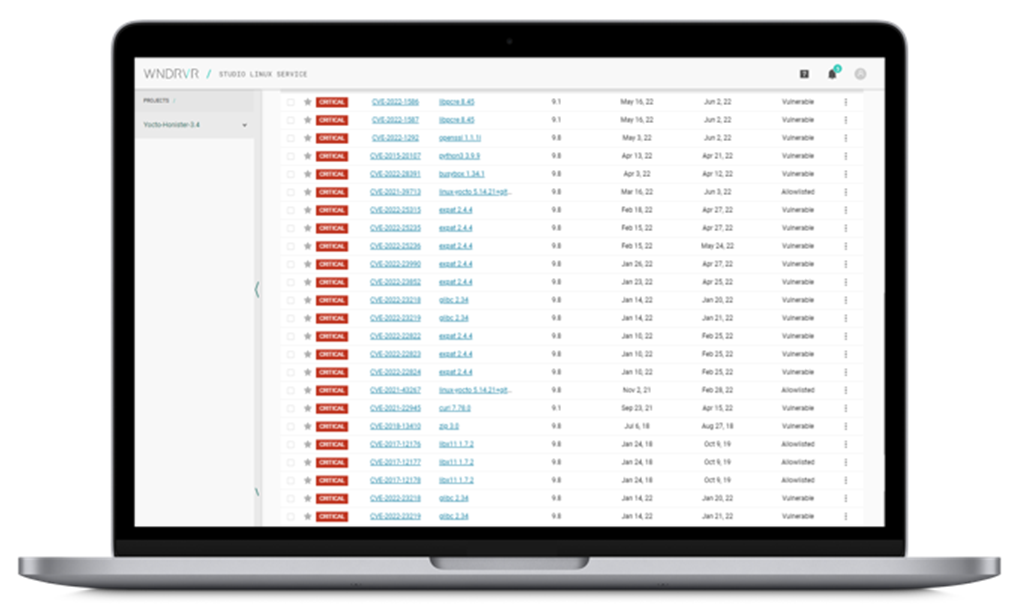
As mentioned before, however, repeated assessment is crucial to ensuring that known risks aren’t re-introduced into the software code. It’s very common for an older package or software component to be linked or compiled into an application, particularly when there are other software or hardware dependencies that require it. Wind River vulnerability scanning can save the list of high priority CVE’s to ensure they are assessed on a continual basis. Having this level of visibility is critical to adequately assessing risk for a Linux platform or application.
6. Automated License and IP Compliance Identification
Not all risks come in the form of software vulnerabilities. With modern software applications containing an estimated 80% open source and third-party software components (Synopsys, 2021) the security risk is clear. But those open-source packages also include license restrictions and usage guidelines that can have significant penalties and impact if not adhered to.
Running IP and license scanning can be time-consuming if not automated. Fortunately, standardizing on a format like SPDX for package descriptions and maintaining a disciplined software bill-of-materials enables developers to implemented automated scans for license use and compliance.
7. DevOps Integrations
Imagine a scenario like this: In a traditional waterfall development model, a development team completes work on their platform or application, at which time it is handed off to a release team to perform some validation prior to general availability or shipping to manufacturing. The release team performs vulnerability scanning and identifies fundamental security risks with several of the open-source packages used in the software stack. They have no choice but to send the application back to development to resolve the vulnerabilities, and the project falls behind schedule due to the rework.
This scenario is not uncommon and is an expensive way to address security vulnerabilities! Much of the benefit of DevOps and “shifting left” has been to implement automation, such as vulnerability scanning, that catches risks early in the development cycle, at a time when implementing fixes is more streamlined and less expensive.
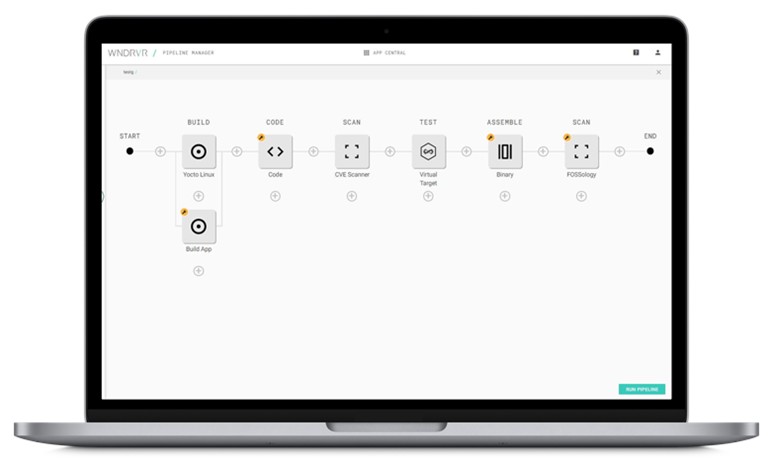
By implementing automated vulnerability and CVE scanning early in the build process, it makes developers responsible for fixing known security risks early in the development phase. This, in turn, delivers several benefits for the product lifecycle in general, including higher security posture and a more agile model for responding to identified security issues.
8. Dashboards and Health Monitors
As we move into an integrated world with applications becoming more and more Internet-enabled, there is a growing need to move from siloed information and offline content to a consolidated view of health, status, and security monitoring. While search engines and various vulnerability databases are helpful, development teams and engineering leadership need a consolidated, streamlined view of their platform and application status rather than having to hunt for and collect information from different sources.
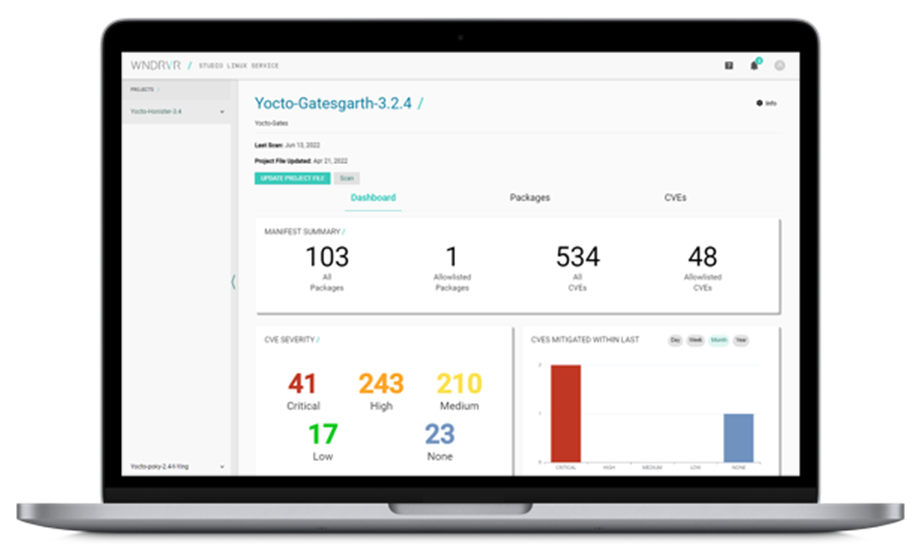
Dashboards are a critical way to see this consolidated view. Good, meaningful dashboards should provide a high-level view of status, be understandable at a glance, all while enabling drill-down and detailed reporting where necessary. Dashboards should also be updated by automation, so they are not stale and out-of-date.
9. Reporting
As software and hardware supply-chain risk is increasingly at the forefront of customer concern, many end users are requiring suppliers to provide transparency and reporting into their security validation methods. Customers may require additional information about security assurance from their suppliers, and nowhere is this more apparent than with vulnerability assessment. Customers have an expectation that suppliers are validating their system components against known vulnerabilities because they in turn are being expected to prove that devices they offer are secure.
While security reporting can be a time-consuming activity, much of this can be generated by strong CVE scanning automation and consolidated data aggregation. Development teams are often finding it necessary to invest in automation that show CVE detection and resolution times. They may be also required to show the criticality of found CVE’s, particularly for high-impact packages within the system.
10. Security and Privacy
Implementing a mature CVE scanning capability brings with it great benefits, but it also introduces a security risk. Any tool that houses information about known vulnerabilities in a Linux platform or application, outstanding CVE’s that may not have been resolved yet, could be exploited by an attacker to target weak points (or identified vulnerabilities) in the software stack. Any CVE scanning tool you use should be secure and from a trusted vendor.
There are three characteristics to keep in mind when evaluating a secure solution for CVE scanning:
1) Access Control: The tool should provide strict access controls to prevent unauthorized access to this sensitive information.
2) Manifest Protection: The tool provider must protect the assets that are being scanned for CVE’s – usually source code and/or software packages. These manifests must be protected to ensure your SBOM and other sensitive information about the components of the Linux platform or application don’t fall into the hands of bad actors.
3) Customer Privacy and Protection: The tool should not compromise the relationship between the supplier and customer. This relationship should remain private through various mechanisms, whether that is encryption, access controls, or other means of obfuscation.
Expert Guidance from Wind River
Using CVE scanning automation can be a powerful way development teams can find vulnerabilities, but often the hardest part isn’t finding them but fixing them. Knowing which patches apply to which versions, recommended upgrade paths, and security engineering techniques to adequately address vulnerabilities can be difficult to say the least.
The Wind River Studio Linux Services team has been guiding customers on security engineering best practices through countless projects, and can bring that expertise to bear for your Linux platforms, applications and systems. In addition, Wind River maintains recommended patching for Yocto Linux and Wind River Linux to ensure your operating systems are always up-to-date and patched to correct known vulnerabilities.
Wherever your organization is on its journey to Vulnerability Management, Wind River Studio Linux Services can help. Whether it’s identifying CVE’s through Wind River’s curated CVE database especially designed for embedded systems, or resolving tricky security risks in your products by partnering with our Studio Linux Services team, Wind River is your security partner. Learn more about how to take action from CVE discovery to mitigation and remediation in our recent webinar, THE PATH TO SECURE LINUX.


